I’ve been watching Android mature over the past few years, and with KitKat’s release last year, I was actually quite intrigued and finally got a fully featured Android device: the Nexus 7. This is possibly the best affordable Android tablet to date. With Lollipop released, I wanted to see if I could get used to a stock Android experience and perhaps pick up a phone running Android. It was mostly smooth sailing, but there was an issue if I wanted to actually get an Android phone as my main device: I found permissions pretty problematic, to a point where I couldn’t see myself using this operating system for my day-to-day use.
Last year, right after KitKat’s public release, I was looking into Android as I was building Cordova applications, which had to run on both iOS and Android. For me to be able to support Android, I needed to check it out again. After a serious look at the system, I was pretty impressed at the progress Android had made in the previous two years. The last time I had used Android at the time, was when I was still running around with a cheap Android handset (the Galaxy Gio) which ran Android 2.2. I replaced that phone a while later with the now two-years-old iPhone 5.
So far, there is one issue that has kept me from trying out an Android phone as my primary driver, and that’s how permissions are handled on Android. I want to talk about that.
The evolution of privacy controls on iOS
I’ve been using iOS since iPhoneOS 2.0 on my first iPod touch seven years ago, and each iteration of iOS has improved privacy controls.
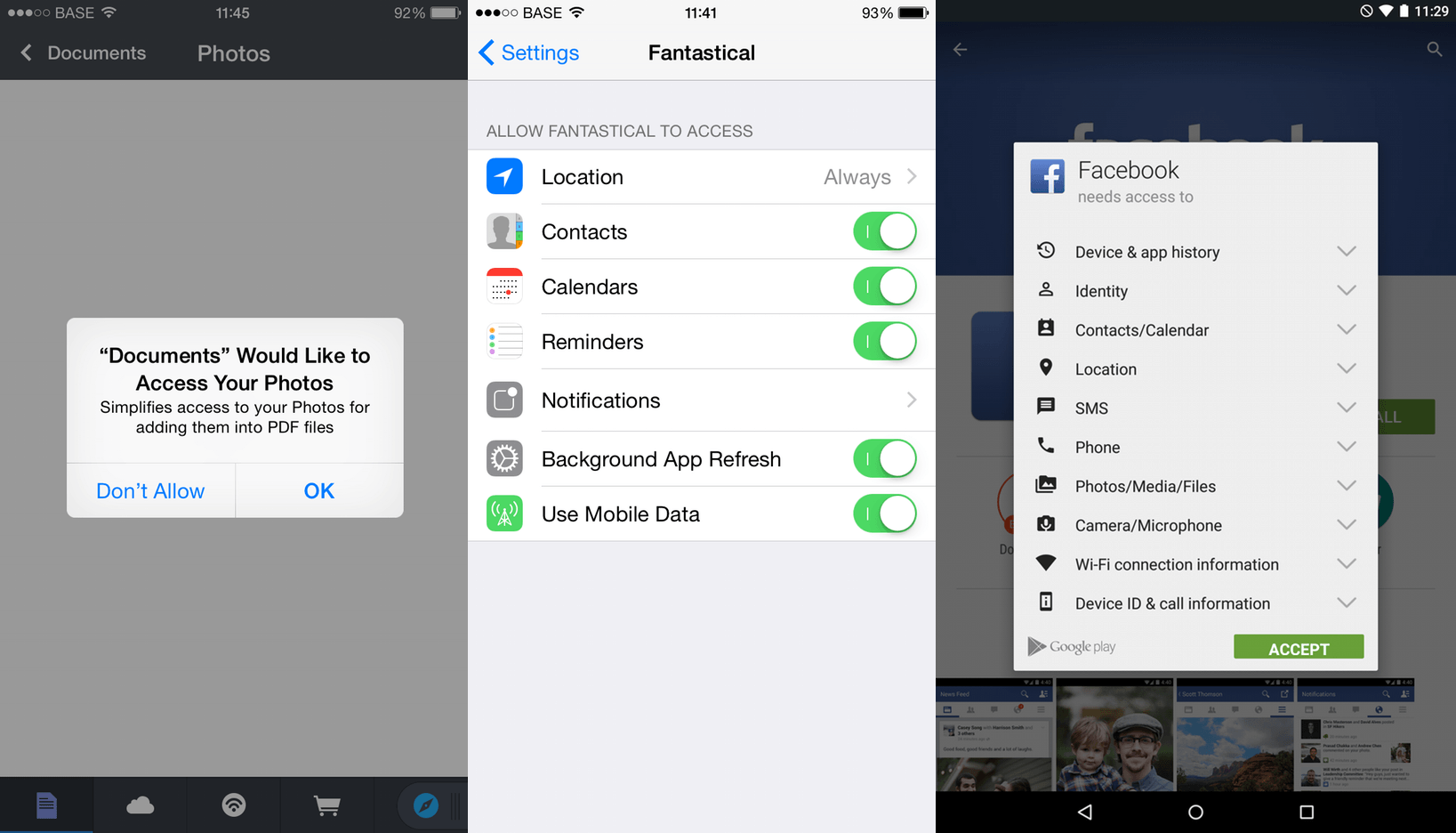
Starting in iOS 4, apps that required access to location data or wanted to push notifications, needed to ask the user’s permission to be able to do this. iOS itself puts up the dialog box, so it’s not optional. Here’s a great video where Steve Jobs explained how they think about privacy at Apple. When Walt Mossberg asked him about the privacy scandals1 that had happened that year (in 2010), Steve explained Apple’s vision on privacy. This is what he said:
“Silicon Valley is not monolithic. We’ve always had a very different view of privacy than some of our colleagues in the Valley. We take privacy extremely seriously. As an example: we worry a lot about location in phones. We worry that some 14 year old is going to get stalked and something terrible is going to happen because of our phone. And so, as an example: before any app can get location data, we don’t make it a rule that they have to put up a panel and ask, because they might not follow that rule. They call our location services and we put up the panel. It’s saying: ‘This app wants to use your location data. Is that okay with you?’ Every time they want to use it. We do a lot of things like that, to ensure that people understand what these apps are doing. That’s one of the reasons we have the curated App Store. We have rejected a lot of apps that wanna take a lot of your personal data and suck it up into the cloud. A lot. So, a lot of people in the Valley think we’re really old fashioned about this. Maybe we are, but we worry about stuff like this.”
When Walt Mossberg brings up moving to the cloud, Steve adds to his previous statement:
“Privacy means people know what they’re signing up for. In plain English, and repeatedly. That’s what it means. I’m an optimist: I believe people are smart, some people want to share more data than other people do. Ask ‘em. Ask ‘em every time. Make them tell you to stop asking them if they get tired of you asking them. Let them know precisely what you’re going to do with their data. That’s what we think.”
This vision was expanded in later versions of iOS: today, on iOS 8, your app can will prompt you for anything that might expose personal information, including: contact information, access to your photo library, access to your location, access to your camera and microphone. There’s also permissions to limit background activity and push notifications for apps, so you don’t get annoyed at an app using too much energy in the background or an app sending you too many notifications.
In addition to those settings, you can also set these on a global level, as well as some extra permissions, like toggling mobile data use on a per-app basis. This means you can disable apps from using your mobile data connection.
iOS Security whitepaper
There’s quite the impressive whitepaper on iOS security out there. I won’t go through all the details, but you should definitely read the whitepaper if you are a developer who is interested in security and encryption.
The link I provided here is recent as of iOS 8.1. From their whitepaper:
Apple designed the iOS platform with security at its core. When we set out to create the best possible mobile platform, we drew from decades of experience to build an entirely new architecture. We thought about the security hazards of the desktop environment, and established a new approach to security in the design of iOS. We developed and incorporated innovative features that tighten mobile security and protect the entire system by default. As a result, iOS is a major leap forward in security for mobile devices.
It’s clear that Apple never intended to expose the filesystem to the end-user, not even to developers. On Android, that’s a different story entirely. I’m not saying Google is wrong for doing that, but from a security point of view, it could be considered a vulnerability. It could also be seen as a layer of complexity: it’s not easy to use a filesystem on a mobile device. But it certainly is useful, as I have noticed during my time with the Nexus 7, although only on a superficial level.2
Another key point that is interesting in the whitepaper is the role of encryption on iOS. Fortunately, Android 5.0 now also supports system-wide encryption (and it’s automatically enabled on the newest Nexus devices), which iOS has had system-wide since iOS 7. If you had a passcode or TouchID set up, you have encryption set up on your iOS devices. Now that Android supports this, it strengthens their case for being good with privacy, but it doesn’t solve their permissions problem, unfortunately.
Android: Demands, not permissions
On Android, the story about permissions is a bit different than what it is like on iOS. Apps have always required permissions when you install them. It’s just a list, and you have to accept these permissions.
I repeat, you have to accept them for the app to install. You cannot use the app without accepting all the permissions. Before Android 4.4, Google actually had a (fully functional) configuration utility for Android that allowed you to modify permissions. But this functionality disappeared in the final build of Android 4.3, and there is still no option to change or modify app permissions in Lollipop, one major Android version later.
Internet access permission
The internet access permission is also unique to Android. This is useful in scenarios where you used offline ad-supported apps that offered no paid ad-free upgrade. This way, you could just disallow internet access and boom: the app is, in many cases, ad-free. This is where Android had a leg up, and it’s deprecated since Android 4.0.3
But wait…
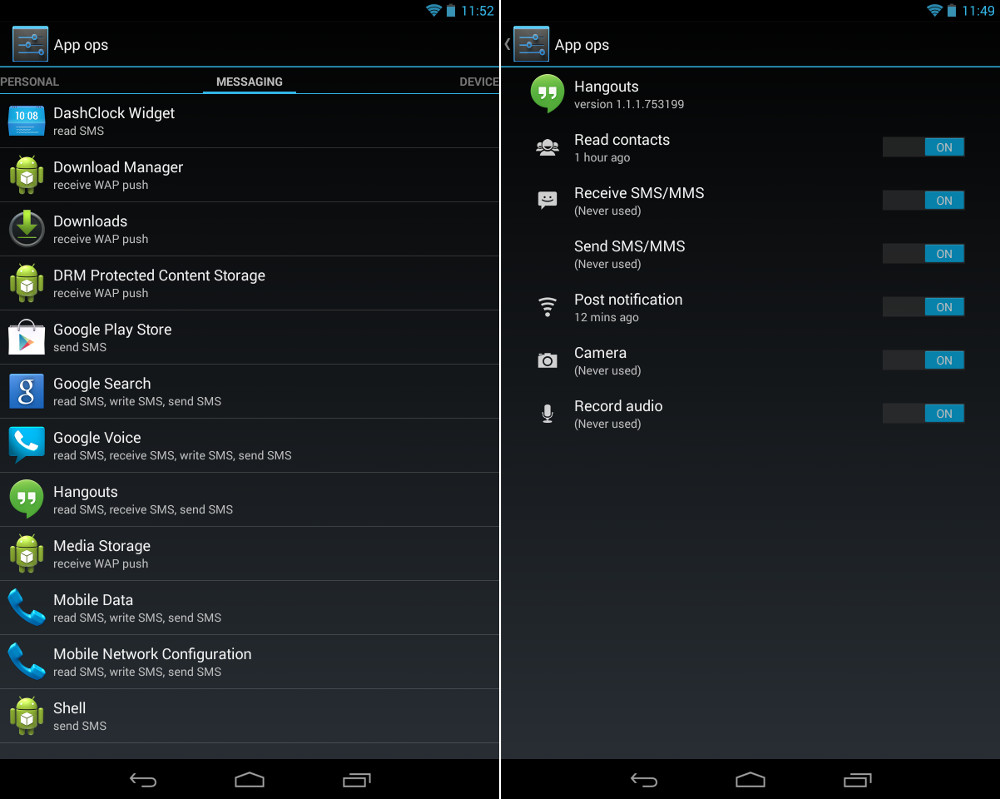
Right now, there’s a bunch of Android experts yelling at me right now. But hold on, I can hear you say, it is possible to completely manage permissions on Android, after rooting your phone!
So yes, there are solutions available on the Play Store. One of them is AppOps. Unfortunately, AppOps cannot allow or disallow access to permissions for system apps. (They might be able to fix this, and I would imagine this will only work if you are rooted.) The problem is that these applications break when large system updates are released. Were Google to build that into the OS, system upgrades wouldn’t pose a problem for the people who want to tweak app permissions.
Let’s talk about rooting and jailbreaking
So yes, it’s absolutely true. If you have rooted your phone, you can use third party apps that completely modify permission access. (If you’re wondering what rooting is, keep reading. If you already know, keep reading regardless.) I wanted to write a different post about jailbreaking and rooting, but I included it here since it’s relevant to the article. Rooting your phone leaves its system files open (and possibly, in some scenarios, vulnerable), since you have now been given total control to everything on your phone. You can even write to (and modify) system files, which are restricted by default, so your system cannot be compromised. By rooting, you’re removing this layer of protection.
Rooting is the process of allowing users of smartphones, tablets and other devices running the Android mobile operating system to attain privileged control (known as “root access”) within Android’s sub-system.
The thing is, geeks like me will want to root their phones if they really want to manage permissions. As long as you know what you’re doing and you’re really careful, rooting isn’t much of a security risk. (Security is a nice fallback, but in the end, it’s just a crutch to avoid problems.) In the end, though, it leaves your phone open to vulnerabilities that might be exposed, and those aren’t always under your control.
But you can jailbreak iPhones too
But hey, isn’t jailbreaking your device kind of similar to rooting? You’re exposing your entire system if you don’t pay any attention. The only thing different is that Google doesn’t mind rooting (they even have apps on their store that require root access), whereas Apple doesn’t support jailbreaks.
You can debate about the names (“jailbreaking” sounds worse than “rooting”), whether one is better than the other, and functionality-wise: from a security point of view, from an ease-of-use point of view, and from a power-user point of view. Feel free to draw your own conclusions.
Jailbreaking is a form of privilege escalation, and the term has been used to describe privilege escalation on devices by other manufacturers as well. Android rooting is the process of allowing users of smartphones, tablets, and other devices running the Android mobile operating system to attain privileged control (known as “root access”) within Android’s subsystem.
The fact remains that rooting and jailbreaking are actually the same thing, with just different names slapped on the process. You’re exploiting a weakness in the operating system to gain total control of the device.
I want to use my phone, not tinker with it
Well, why don’t you root your tablet, then? You are a developer and a geek. You know your way around Android already, you know how to use a CLI. That’s what you might be thinking. I considered this as well. But as long as this is a third party fix, there’s no way to guarantee that this won’t change.4
I don’t want to mess with my phone either, I want a great experience out of the box. And having to root my phone in order for me set my privacy settings, just doesn’t cut it for me. I understand that this is enough for a bunch of people, but that doesn’t mean nothing should happen to permissions management on Android. This is why I will probably be sticking with iOS devices at this time.
Sometimes things break when you tinker
I’ve used many Linux distros for a long time. If there is anything I learned during that time, it is that sometimes things break when you start tinkering. I need my phone, I need it to be reliable. It can’t break all of a sudden.
Possible issues
Android’s permissions system could (and should, in my humble opinion) be vastly improved. Of course, there are possible issues that might arise with the implementation or insertion of such a system.
If you’re not gracefully handling permissions, that might mean apps stop working, and that is an issue. Making permissions accessible and understandable to users is another thing. Do regular people actually want this? Perhaps I’m in the minority. I’d even wager that I actually am. But privacy is an important subject that people need to be educated on.
Educating people about privacy
But what about regular people who want to get things done? They don’t want to look into this. They just accept the dialog that says the app can access all their data, and they don’t think about it much. Some people don’t even know what they are agreeing to.5
And that’s just not okay. It should be much easier! For a company such as Google, where open is an important word, I find it hard to believe that permissions can’t be managed from the core. We’ve even got encryption on Android now, but I can’t toggle whether Facebook can access my location? It’s disappointing, because if it weren’t for this, I would have gladly given Android a try.
What this post isn’t: Android vs. iOS
Now, before I end this longer piece, I want to point out a few important things.
First, this isn’t about one system being the best. I enjoy using both operating systems. I enjoy using my iPhone 5, and I enjoy using my Nexus 7. They’re both excellent devices. They both have their strong points. (I just don’t install many third-party apps on my Nexus 7 because of privacy concerns.)
You can get apps via the Play Store that you won’t ever find on the App Store for iOS. For instance, Android has the best video player, hands down, with MX Player Pro, and an amazing emulator option with DraStic.
So, what’s the most important takeaway from this post? Sure, Android has a permissions problem. But what’s more important is the following: we need to educate everyone on security risks of granting blanket permissions. People on both iOS and Android are granting permissions they might not want if they knew what data these apps could access.
Regardless, after everything that happened over the past year with privacy mishaps, I believe we have every concern to be a little bit more careful with our data and what apps do with it.
They’re not disappearing this year, either. iCloud was under fire for a period of time after celebrity images were leaked from what seemed to be an iPhone backup from iCloud. It was later revealed that third parties had gotten access to iCloud accounts via social engineering. (Meaning that Apple wasn’t responsible for the breach. However, they did fix a few possible leaks in their system, including a login form that had no limit to the amount of times you could try to login to iCloud. This issue was fixed not too long after it came to Apple’s attention.) ↩
I find myself using the Android filesystem in kind of the same way I use iTunes to transfer individual files to my iOS devices. Certainly, a filesystem is a bit more convenient since you can create folders, but in the end, it’s not that big of a difference. ↩
I wish this was a setting on iOS. Unfortunately, you can only set mobile data access in iOS, not limit WiFi access. To be honest, it would overkill, because most apps need internet access nowadays. ↩
Or, like I said, break the third-party app when the OS receives an update. ↩
Some people, and I’ve seen this many times, just press “I agree” to any text that pops up on their screen. They do the same for notifications and useful error messages that say something about what went wrong, but they just click them away without reading them. ↩